Tag Computer security - results: 26
As criminals can use artificial intelligence? The most dangerous variant
Artificial intelligence capable of much. For example, it can replace the face of Arnold Schwarzenegger Sylvester Stallone the Last 10 years, every day we hear news about how this or that artificial intelligence has learned new ski...
Technology spy on users: how and why companies collect personal data
App TikTok developed in China, whose government engages in pervasive surveillance of its own citizens. do you think you are being followed? While you ponder the answer, let us recall that almost every action is passive observation...
Apps vs browser: where it is safer to communicate?
What is safer: instant messengers or browsers? the XXI century — age of mobile applications and various social networks by interests. Worrying about the safety of the data of their users, developers from all over the world a...
Who invented the computer password?
What you see when you turn on your computer, laptop or smartphone? If you're a family man, or you important the safety of personal data, most likely, before you open the screen with a field to enter the password from the computer....
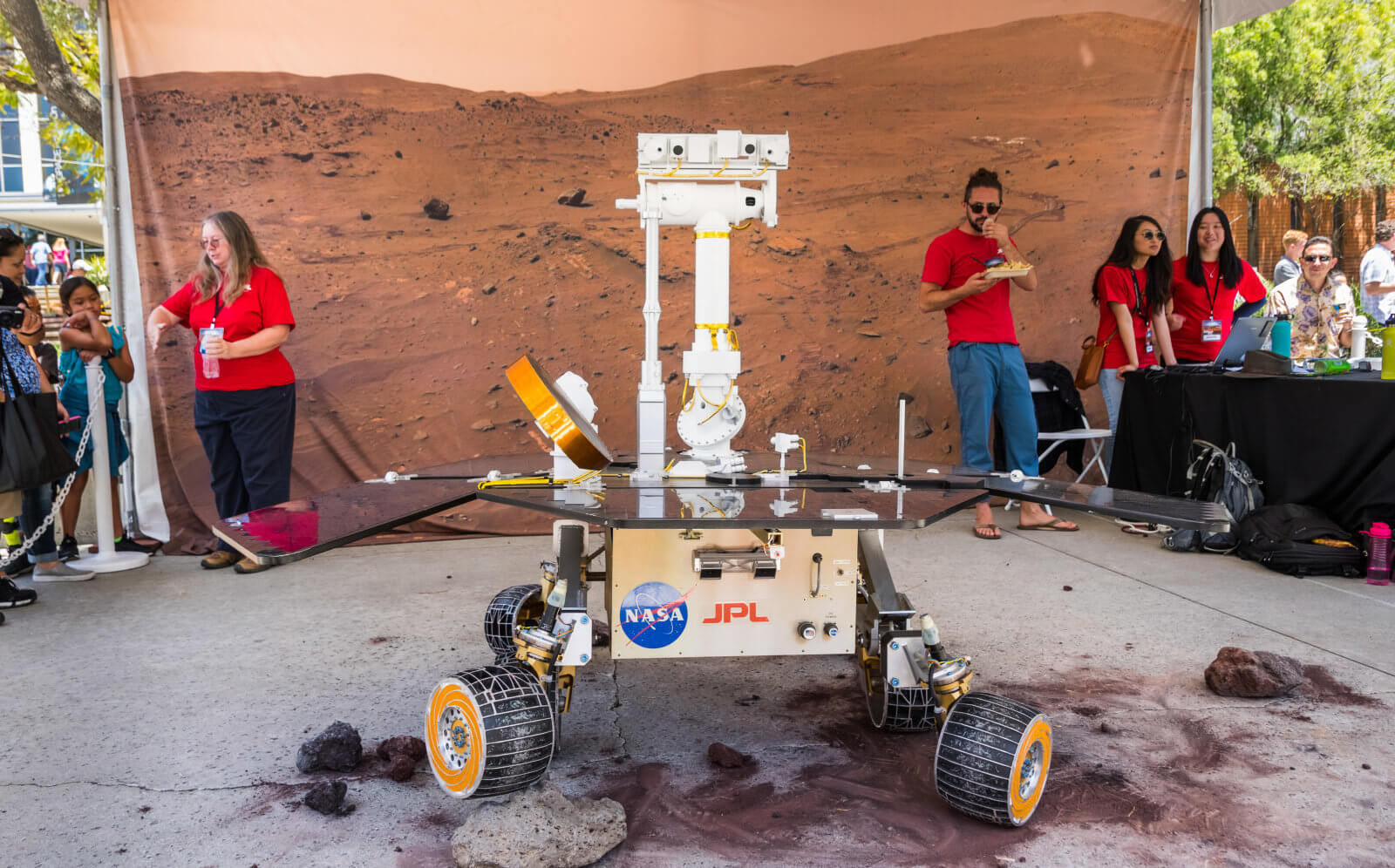
Hackers broke into the NASA server, using a cheap Raspberry Pi computer
Can the U.S. jet propulsion Laboratory NASA (JPL) and produces some of the most high-tech things on the planet, for example, the same and space telescopes, but it turns out that she has experienced very serious problems with cyber...
Algolux introduced the Ion platform, the development of Autonomous observation systems
Algolux, established in 2015, is not yet particularly well-known in a crowded field of automotive computer vision. However, this startup from Quebec attracted the attention of investors. For example, last may the company raised $ ...
USB-C will allow you to identify "your" chargers
-C is being improved and will soon begin to protect smartphones — including from viruses. Future smart phones may begin to learn designed just for them charger. Today mobile devices — mostly smartphones — play i...
The scientists said, can be dangerous quantum computers
Quantum computers are fundamentally different from classic software , and therefore provide a fast interaction with huge amounts of data. At the moment they are underdeveloped, but in the future will certainly raise machin...
How to maintain your anonymity on the Internet (and a good save)
it May seem that lately, VPN services have become very much, but actually their number is slightly increased — just the need for gaining access to the particular site has increased dramatically. Besides, in order to use the ...
IBM will use AI to address problems of cybersecurity
In recent years, hackers and other cybercriminals invent new means to steal data or harm to companies and individuals. And sometimes to protect standard techniques are no longer enough, but to secure cyberspace has solved a major ...
Google wants to "kill" the URL in the name of security users
Google Engineers are going to arrange another reform on the Internet. The Google Chrome browser already eradicates the HTTP Protocol, marking using his sites as unsafe and forcing administrators to move to HTTPS encryption. Accord...
"Kaspersky lab" will not cooperate with Europol
"Kaspersky Lab" has carried out a reversal in the direction of Russia and decided not to cooperate with European law enforcement agencies, including Europol. This is due to the recently adopted European Parliament resolution on st...
Half a million routers can be turned off VPNFilter
Researchers in the field of security recently discovered that at least 500 thousand routers in service among ordinary users and companies infected by malware VPNFilter, the previous version which was previously spread on the terri...
What have you learned about the attack on 200 000 network of Cisco switches?
the Last few days were not the best for cyber security. The Iranian Ministry of communications and information technologies reported that it has also become a victim of global cyber-attacks that (or simply switches) from Cisco, wh...
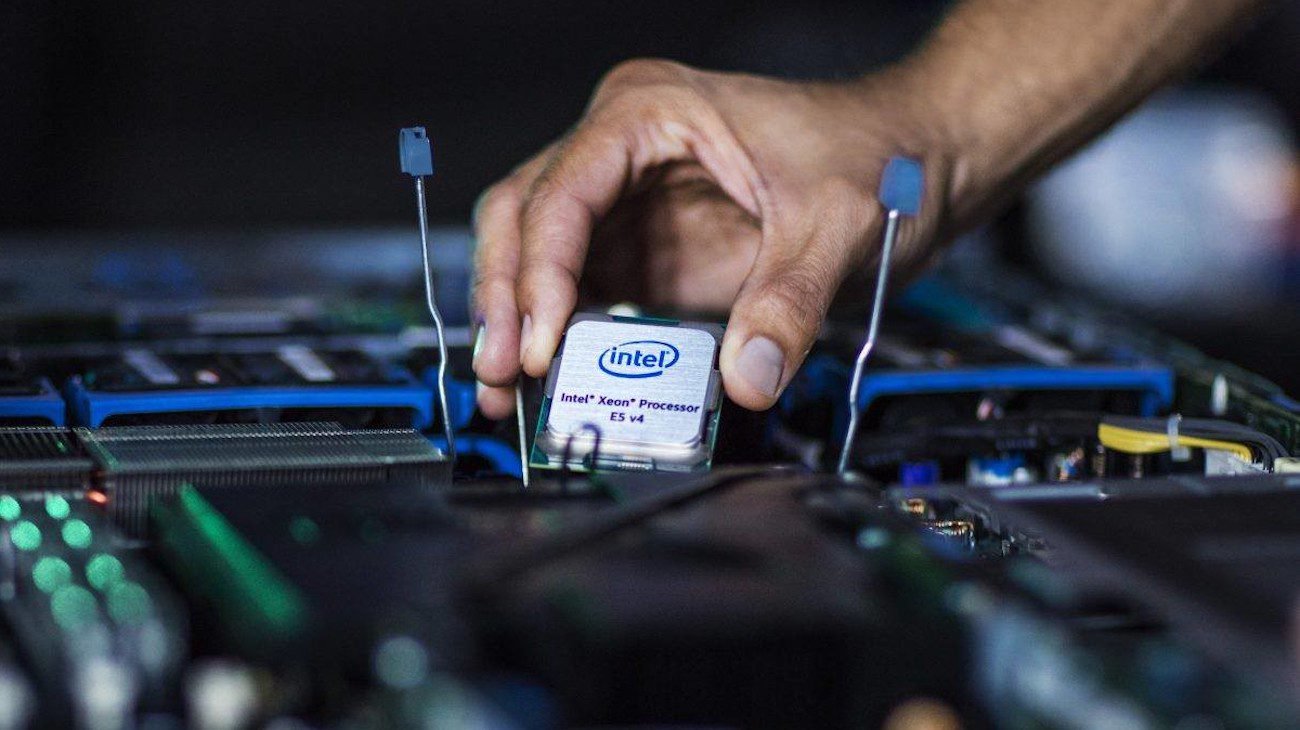
Intel will no longer defend some of their processors from vulnerabilities
At the beginning of this, as of 2018, some processors of Intel was discovered that allowed attackers to steal user data which are processed in the processor. Immediately representatives of Intel said that will work on a "patch" th...
Employees of "Kaspersky Lab" found unkillable computer virus
Almost every day on the world wide web to discover some new computer viruses. And very seldom happens so that viruses cannot be destroyed. Moreover, a rare virus is able to hide the years, from anti-virus developers. But, accordin...
Avast has developed an AI system for the protection of IoT from the rest of the miners
Hidden cryptocurrency is starting to become more rampant. Hackers earn money using for mining other people's computers, smartphones and other «smart» device. At the world mobile Congress company Avast said about the exte...
Servers on Linux and Windows massively affects virus-miner
cybersecurity Experts from companies Check Point, Ixia and Certego found that more than 700 servers on Windows and Linux infected by malicious software RubyMiner used for covert cryptocurrency. The first attack was noticed last we...
DARPA resumed work on the "uncrackable" computer Morpheus
Cybersecurity in recent years has become particularly relevant for investment not only large corporations, but also the military. In light of recent events, when the worm WannaCry suddenly knocked out more than 300 000 computers w...
Named list of the worst passwords of 2017
the Company SplashData, specializing in providing information security services, annually makes the list of most popular passwords, based on millions of stolen logins, which end up in open access. And every year we never cease to ...